In the previous blog post, I discussed how to achieve CSRF attack protection using synchronized token pattern method. In this post, I will be discussing how to do it using double-submitted cookie pattern.
As you can see in the above diagram, in double-submitted cookie pattern two cookies (for the session and for the csrf token) are stored in the browser.
In our previous method, we stored csrf token values on the server side (text file). But here we don't do it.
Sample website created for this is uploaded to my Github and the link is mentioned below.
https://github.com/sajith01prasad/Cross-Site-Request-Forgery---method-02.git
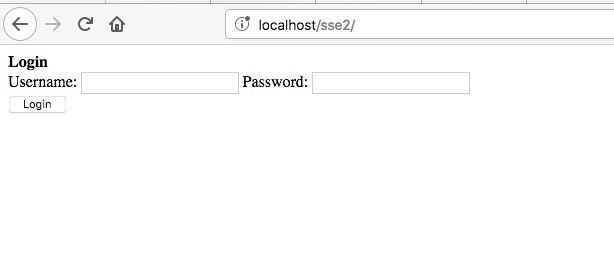
index.php
once this page gets loaded on the web browser user sees a simple login form. Username and password are hardcoded in the code.
result.php
As you can see two cookies are stored on the browser. These cookies have 1 year expiration time and they are accessible from anywhere.
Javascript function is written to retrieve the csrf value from the csrf cookie set on the browser. Then DOM will be modified with the value that is retrieved from the csrf cookie.
home.php
csrf cookie value and the html hidden field csrf value are sent to the checkToken function as parameters.
token.php
This function returns true if the csrf token values get matched.
This is the second way of protecting your website from csrf attacks with the help of double submitted cookie pattern.
Thank you.






No comments:
Post a Comment