Thursday, May 10, 2018
Cross Site Request Forgery - method 01
What is Cross Site Request Forgery?
Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated. CSRF attacks specifically target state-changing requests, not theft of data since the attacker has no way to see the response to the forged request.
In this blog post, I will be discussing a method that can be used to protect your own website by generating Cross-Site Request Forgery Tokens in server side and validating them before respond to any client request.
The sample website source code is uploaded to the GitHub and you can download it from there. The link is mentioned below.
https://github.com/sajith01prasad/Cross-Site-Request-Forgery---method-01.git
I will be using code screenshots of .php files to explain what happens inside the code.
There are 5 .php files and one. txt file.
What does this website do? User logs into the website using his/her credentials (username and password are hardcoded "sajith", "sajith"). Upon the log in a session will be created and the session id will be used to map with the CSRF token that will be generated along with the session creation.
Then the user redirects to a web page that allows the user to update a post. When this page loads with the help of AJAX, generated CSRF token value will be added to a hidden field in the HTML form.
Once the user updates a post CSRF token will be validated. If it is valid user will see the post he updated......
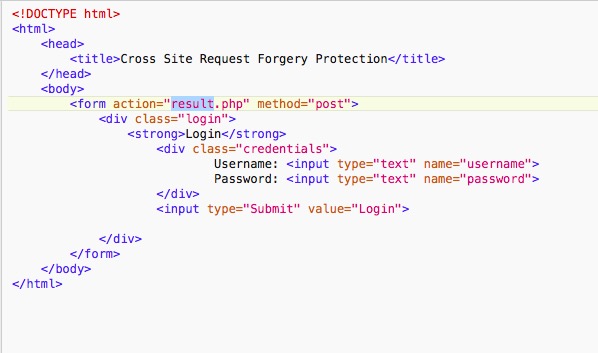
index.php
Once the form is submitted result.php will be called.
result.php
A simple php code is written on top of the page to validate the user inputs.
As you can see Ajax is used call the csrf_token_generator.php file to get the generated CSRF token value and put it inside the hidden textfield in the HTML form.
csrf_token_generator.php
This php file generates the csrf token. Also it sets a browser cookie with the value of session_id. After that CSRF token value will be stored in a text file called Tokens.txt along with it's session_id.
openssl_randon_pseudo_bytes() is used to generate the 32bit long csrf token. In order to use this function you have to have openssl installed. Otherwise it will give you an error. The generated value then converted into it's base64 value using base64_encode() function in order to make it more secure.
token.php
this php file has checkToken function which gets two parameters (csrf token and session id) and return true if the given parameters matches with the values that are stored inside the text file.
Tokens.txt
home.php
This is where checkToken function gets called.
There are many ways to protect your website from CSRF attacks. In my next blog post I will be discussing another method to achieve this. Have a good day people!!!
Subscribe to:
Post Comments (Atom)










n904d5saavq725 japanese sex dolls,vibrators,sex chair,wolf dildo,Rabbit Vibrators,pink dildoe,realistic dildos,vibrators,wholesale sex toys w823m9cfwbg257
ReplyDelete