Wireshark is the most widely used packet analyzer in the world. What can we do with this tool? Actually there are limits. If you think that you can hack into a system using wireshark that is not the case. You can actually gather information which you will need to hack into someone's system or account using Wireshark.
Visit this link to download the latest version of Wireshark.
https://www.wireshark.org/#download
Download and install the wireshark according to your system preferences.
Fire it up. You will see this user interface.
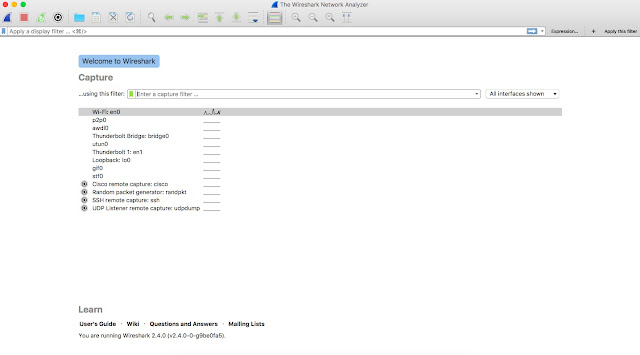
You can see all the network interfaces in your device such as WLAN, eth0 , p2p0.
If you are using Wifi just enable Wifi only. Do not enable other interfaces. Because then it will become hard for you to find expected output in results.
Once you click on start button Wireshark will start monitoring wifi traffic.
At the top of the GUI you will see a search bar called filter. This text box is very useful if you are a newbie to Wireshark. There are hundreds of filter commands out there you can use when doing your information gathering.
From this point onwards we will be looking at how to use Wireshark effectively.
Visit a website which as a login form. (Wireshark has to be on)
Now log in. After you try username and password come back to Wireshark and stop the capturing.
In the filter section type "frame contains username".
You can right click on the login form and check the textbox names. (eg- username). Otherwise filter will not work.
Now wireshark will extract only the packets which contains username out of the result. This will make you stop wasting time going through each and every packet in the result.
As you can see there are only 4 packets in the results now. Now for next step it is important to have a little bit of understanding on how TCP 3-way handshake works.
This can be used to identify packets when you are analyzing manually. How can you know whether a particular packet is sent by you or received by you(request or reply)? You can identify these things with the help of SYN, ACK values.
Right click on each packet to go through its tcp stream.
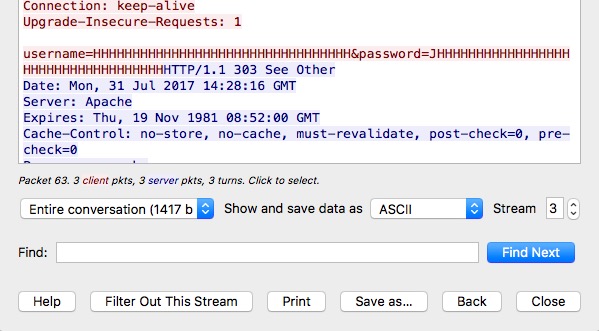
You will find username and password you entered in the TCP stream( The login site you used has to be served on HTTP).
What if someone installs Wireshark on his machine and you log into one of your accounts using his machine without knowing Wireshark is there? He can get your login credentials and log into your account at anytime he wants.
These are important filters you should know.
1) Obtain only genuine http request of the given logs.
http and tcp
2) Search for a particular IP.
ip.addr == <ip_address>
3) Search for a packet which contains an image
frame contains <name>.gif
4) ARP packet from 00:0b:86:6e:69:68 to 80:56:f2:25:63:40
arp and frame contains 00:0b:86:6e:69:68
5) To display HTTP packets with source or destination IP address equals to <Some IP>
http and ip.addr==<IP_address>
6) To display packets with source port equals to <portnumber> and destination port equals to <port>
filter - tcp.srcport eq <portnumber> and tcp.dstport eq <port>
7) To display packets with a TCP SYN flag.
filter - tcp.flags.syn == 1
8) To find the authentication username and password
filter - http.authorization
I hope you guys learned something from this blog post. Cheers !